How to Perform A Cyber Security Risk Analysis
Performing a cybersecurity risk analysis helps your company identify, manage, and safeguard data, information, and assets that could be vulnerable to a cyber attack. Such analysis helps you identify systems and resources, determine the risk, and create a plan for security controls that can help protect your company.
Meet With A Consultant
It all starts with your FREE consultation. We will discuss your needs and decide together what the best path to cybersecurity compliance is for you.
You may choose to get advice and stop there, or have us work with you to get it accomplished.
Categorize Data
You do not need to treat all your data the same.
There are different levels of protection for:
Public
Internal
Confidential
Regulated
Some data types have federal regulations to follow when handling/storing.
Some of your data may be so critical you cannot survive without it.
Identify Vulnerabilities
Who has access? Who NEEDS access?
Are Username/Passwords shared? Are they written down?
Do you have open Wi-Fi for guests?
When is the last time you updated security patches?
Did you enable any security settings on your data ?
Calculate Risk To The Business
What if the worst happens? Can your business survive?
Consider as many things as possible:
Natural disaster
Employee error
Malicious intent
How likely is it to occur?
What is the consequence if it does?
Develop Cybersecurity Plan
A written plan addressing every vulnerability identified
Data Protection
Personally Identifiable Information
Intellectual Property
Payment Cards
HIPAA Compliance
Computer Security
Mobile Device Security
Internet Security
Facility Security
Employee Training
Implementation Guides
We will work together over a series of Zoom meeting to Implement all the required configurations and changes to your procedures so you can be cybersecurity compliant. We will find the best solutions for you on your schedule at your pace.
Sign Cybersecurity Policy
We will deliver you a ready to sign Cybersecurity Policy for your business.
This includes all applicable Employee Policies and company policies to keep you protected in the future.
Training
Cybersecurity awareness for all employees
New policies awareness
Operational security ”best practices”
Specific training for each person assigned a task
Train management on how to implement new policies
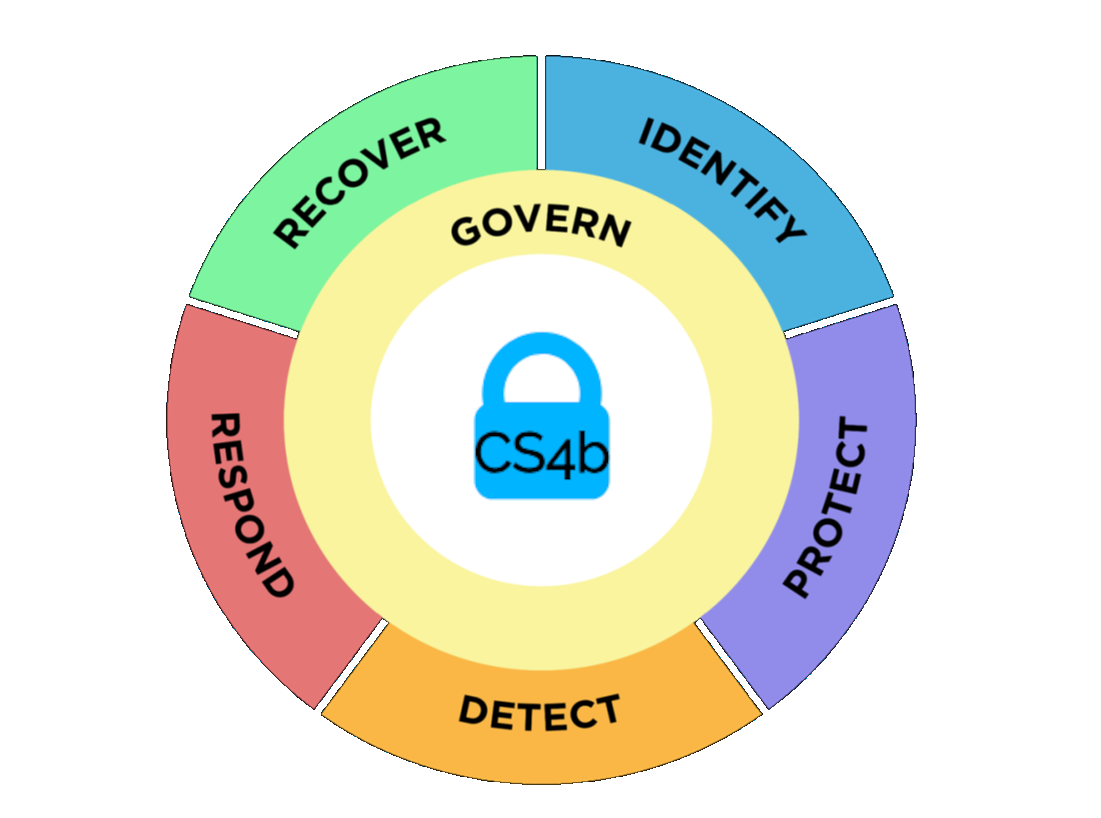
What is NIST CSF and why do we use it?
Although primarily US-based, the National Institute of Standards and Technology Cybersecurity Framework (NIST CSF) has reached international application and is used by several organizations worldwide, and especially in Canada for IT compliance.
In August 2023, the U.S. National Institute of Standards and Technology released an updated Cybersecurity Framework with significant changes, including an emphasis on governance and supply chain risk management that align with Canadian legal requirements and regulatory guidance. The updated Framework will be an important benchmark resource for Canadian organizations of all kinds and sizes.
There are no "silver bullets" when it comes to cybersecurity and protecting an organization. For instance, "Zero-day" attacks exploiting previously unknown software vulnerabilities are especially problematic.
However, using the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) to assess and improve management of cybersecurity risks will put your organization in a much better position to identify, protect, detect, respond to, and recover from an attack, minimizing damage and impact.
NIST CSF will enable you to meet or exceed all government mandated cybersecurity regulations like HIPAA, GLBA, PCI-DSS, FINRA, SOX, CMMC, ITSG-33, ISO 27001, and many others.
Not just a software solution, it also uses governance, processes, and awareness
Enable long-term cybersecurity and risk management
A framework that keeps you compliant effortlessly
A framework that is flexible and easily adaptable regardless of size and type of your business
Scalable to grow as your business grows and is a valuable to build trust with your customers
Helps your organization achieve a global standard of cybersecurity
The NIST CSF 2.0 organizes basic cybersecurity activities at their highest level with these 5 functions.
-

Document your assets (hardware, software, people, and critical processes).
Assess the potential impact of a total or partial loss of critical business assets and operations.
Assess cybersecurity risks posed by suppliers and other third parties before entering into formal relationships.
-

Assessment Questionnaire
Identify and control who has access to your business information
Require individual user accounts for each employee.
Create Cybersecurity Policies (HIPAA Security & Privacy, GLBA/IRS WISP, CMMC SSP & POAM, PCI-DSS, Company Cybersecurity Policy)
-

Limit employee access to data and information
Install and activate software and hardware firewalls on all your business networks
Secure your wireless access point and networks
Dispose of old computers and media safely
Train your employees
-

Advanced Threat Security
Email Security and Antispam
Exploit Defense
Full Disk Encryption
Network Attack Defense
Patch Management
Web Content Control
Web Threat Protection
-

Managed Endpoint Detection and Response
Develop Response Plans for disasters, data breaches, and information security incidents
Repair your reputation
Mitigate damages to your customers
Prioritized Alerts Investigation
-

Full backups and incremental backups of important business information and customer data
Consider cyber insurance
Make improvements to processes, procedures, technologies
Business Continuity Plan